This post is adapted from the Blacksmith Infosec book, Forging Trust.
The NIST Cybersecurity Framework (CSF) is widely regarded as the foundational standard for cybersecurity risk management in the United States and internationally. Originally developed to improve critical infrastructure cybersecurity, the framework has evolved to address the needs of organizations of all sizes and sectors, including industry, government, academia, and nonprofit entities. Its design is outcomes-based and sector-neutral, allowing organizations to tailor its implementation to their specific risks, technologies, and business objectives.
The CSF provides a common language and structured approach for managing cybersecurity risks, supporting risk prioritization, and enabling organizations to assess and communicate their cybersecurity posture.
“NIST Cybersecurity Framework has become the de facto standard for many organizations all over the world, of all sizes, scopes, and industries.” — Summary Analysis of Responses to the Cybersecurity RFI, NIST.gov
Why NIST?
Several factors explain why NIST CSF is considered the baseline:
-
Comprehensive and Flexible: The framework provides a robust set of best practices that are adaptable to organizations of any size or industry, allowing for customization based on unique risks and business goals.
-
Widely Recognized and Trusted: Developed through collaboration between government and industry, NIST CSF is referenced in regulations, procurement, and industry standards, and is often mapped to other frameworks like ISO 27001 and PCI DSS.
-
Risk-Based and Outcomes-Focused: NIST emphasizes risk management and continuous improvement, helping organizations prioritize resources and adapt to evolving threats.
-
Supports Communication and Governance: The framework bridges technical and business teams, supports board-level reporting, and, with the addition of the “Govern” function in CSF 2.0, explicitly addresses governance and alignment with business objectives.
5+1 Explained: The Core Functions of NIST CSF 2.0
NIST CSF 2.0 organizes cybersecurity activities into six core functions, often referred to as “5+1”:
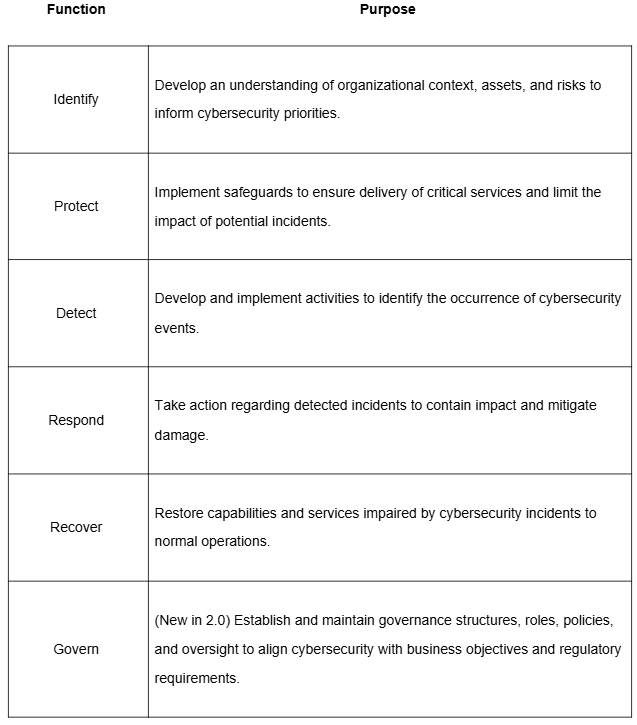
As you can see, NIST CSF 2.0 is structured around six core functions, each representing a critical aspect of an effective cybersecurity program. This includes the original five pillars from NIST CSF 1.1 — Identify, Protect, Detect, Respond, and Recover — and introduces a newly added “Govern” function.
The addition of the “Govern” function in CSF 2.0 reflects the growing importance of cybersecurity governance, ensuring that risk management is embedded at the highest levels and aligned with organizational strategy.
All told, NIST CSF’s flexibility, comprehensive coverage, and global recognition have made it the go-to framework for organizations seeking a practical, effective, and scalable approach to cybersecurity risk management in general circumstances
When Does NIST Apply?
The NIST Cybersecurity Framework (NIST CSF) applies in a wide range of circumstances due to its flexible, voluntary, and sector-neutral design. Organizations choose to use NIST CSF when they want a structured, outcomes-based approach to managing cybersecurity risks, regardless of their size, industry, or maturity level. The framework is especially relevant in the following situations:
-
Building or Improving a Cybersecurity Program: NIST CSF provides a foundational structure for organizations starting to develop a cybersecurity program or seeking to enhance existing practices. It serves as a roadmap for aligning security activities with business objectives and risk tolerance.
-
Risk Management and Prioritization: The framework is used to identify, assess, and prioritize cybersecurity risks, helping organizations allocate resources effectively and make informed decisions about security investments.
-
Regulatory and Industry Alignment: While adoption is voluntary, NIST CSF is often referenced in regulations and industry standards, particularly in critical infrastructure, finance, and healthcare. Organizations may use the framework to demonstrate compliance with regulatory requirements or to align with best practices recognized by regulators and industry groups.
-
Supply Chain and Vendor Risk Management: Organizations use NIST CSF to evaluate and manage risks associated with third parties and supply chain partners, ensuring consistent security expectations across business relationships.
-
Communication and Governance: The framework supports clear communication about cybersecurity between technical teams, executives, and stakeholders, and helps integrate cybersecurity governance into enterprise risk management.
-
Continuous Improvement and Benchmarking: NIST CSF enables organizations to assess their current cybersecurity posture, set target goals, and measure progress over time, supporting continuous improvement and benchmarking against industry peers.



