MSPs and Incident Response Plans — An Overview

For Managed Service Providers (MSPs), incident response planning is a critical part of cybersecurity preparedness. With cyber threats targeting not only their own infrastructure but also their clients’ systems, MSPs face unique risks and high stakes when it comes to incident response. Having a clear, actionable incident response plan can mean the difference between business […]
Rising Regulatory Pressure on SMBs: Why Compliance is Now a Critical Priority
It’s become a standard refrain in industry forums and vendor webinars: demand for compliance services is skyrocketing for managed service providers (MSPs) and their clients. But have you ever wondered exactly why this is happening? The answer isn’t just about headline-grabbing breaches or new technology — it’s about an unprecedented surge in regulatory pressure that’s now […]
Cyber Insurance and Compliance: The New Gatekeepers

Cyber insurance was once viewed as a safety net — merely a way for businesses to transfer risk in the event of a breach or ransomware attack. But that safety net is tightening. Rising premiums, stricter exclusions, and growing demands for evidence of security maturity mean that insurance is no longer a backstop you can […]
Compliance: Make 2025 the Last Year of Spreadsheets

It’s no secret that spreadsheet-driven compliance management is becoming obsolete. They might be familiar and easy to use, but spreadsheets introduce significant (and often hidden) risks that threaten operational efficiency, audit success, and security posture. The Risks of Spreadsheet-Based Compliance Spreadsheets rely heavily on manual data entry, which is inherently error-prone — any oversight can […]
Semi-Autonomous Security Operations: How AI and Humans Team Up

Semi-autonomous security operations are reshaping how organizations defend against evolving threats, marrying the strengths of AI-driven platforms with the irreplaceable judgement of human analysts. Advanced Security Operations Center (SOC) tools now automate initial triage, evidence gathering, and even aspects of incident response, enabling faster, around-the-clock threat detection and significantly reducing repetitive manual toil for security […]
Stay Ahead or Fall Behind: Continuous Monitoring as a New Security Standard
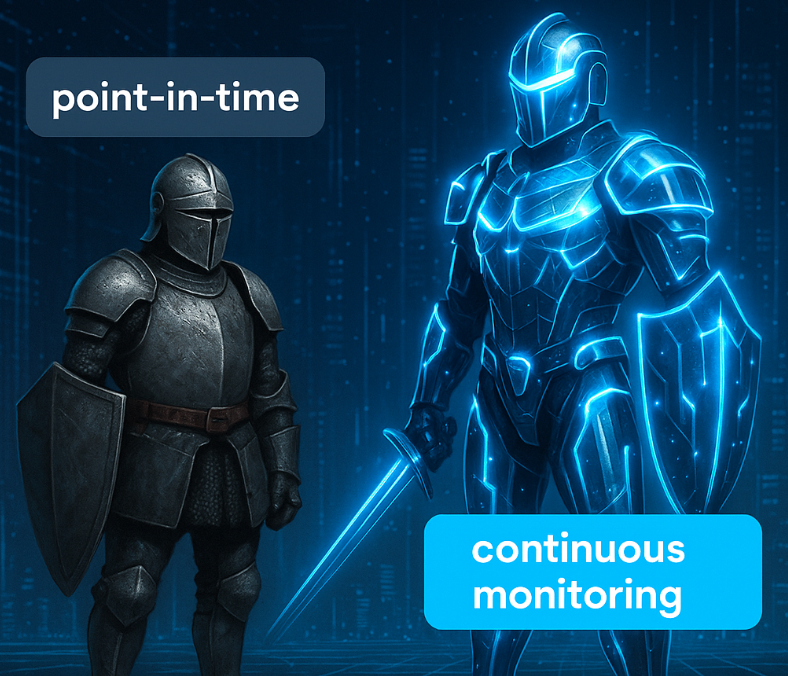
Compliance has long relied on point-in-time audits — structured reviews conducted annually or semi-annually to check if organizations meet regulatory requirements. But as cyber threats grow more dynamic and regulators demand real-time assurance, that model is increasingly inadequate. Continuous monitoring is becoming the new standard, offering organizations a more proactive and resilient approach to compliance. […]
Insider Threats in a Hybrid Workforce: What to Watch for in 2025

Insider threats — malicious, negligent, or even accidental breaches performed by trusted individuals — have evolved rapidly with the rise of distributed teams and the proliferation of hybrid work models. Organizations face a growing challenge: how to safeguard sensitive information when employees, contractors, and partners operate remotely, often with less oversight and on diverse networks. […]
Rise of Voice Phishing: AI-Powered Vishing Targeting Enterprise CRMs

AI-powered voice phishing, or “vishing,” has emerged as a top threat by bypassing email filters and traditional controls to directly target employees through convincing, real-time social engineering. In 2025, several high-profile breaches demonstrate that vishing’s evolution — combining AI voice synthesis, CRM targeting, and publicly scraped data — is redefining the cyber risk facing corporations […]
Turning Compliance Into Opportunity: How Blacksmith Fuels MSP Growth
If you’ve scrolled any cybersecurity headlines in 2025, you’ve noticed a trend: “Lack of compliance” isn’t just a technicality — it’s become a key cause of major breaches across industries. The growing scrutiny is clear: when organizations are hit, the first big question reporters, regulators, and clients ask is, “Were they compliant?” Breaches, Compliance, and […]
Securing the Expanding Attack Surface: From IoT to 5G
The explosion of connected devices and faster networks is fundamentally redefining cybersecurity in 2025. With millions of new IoT devices deployed in fields ranging from manufacturing to healthcare, and 5G networks rapidly scaling up worldwide, organizations now face a vastly widened attack surface. Hackers are quick to target these new entry points—and without proactive defense, […]
