Blue Team vs. GenAI Attackers: What Actually Changes at the Keyboard

What’s the full story when it comes to AI-powered cyberattacks? Blue teams are not suddenly fighting alien TTPs; they are fighting familiar kill chains with the volume turned up and the dwell time compressed. The real change is how both sides use the keyboard: attackers to iterate faster, defenders to triage and decide faster. From […]
Why Security Culture Beats Security Tools (And Makes Them Worth What You Paid)

Security culture beats security tools because tools only amplify the behavior you already have. A great stack in the hands of a rushed, over‑pressured organization just turns bad habits into faster, louder failures. A modest stack inside a culture that takes security seriously will almost always outperform it. Breached with everything “turned on” Picture the […]
Surviving Supply-Chain Ransomware As An MSP

Supply‑chain ransomware has turned MSPs into high‑value dominoes: hit one provider, get dozens of downstream victims as a bonus. In this article, we’ll discuss how to defend your own house, constrain vendor blast radius, and explain the risk in plain English to SMBs. Why MSPs Are Now Prime Targets MSPs sit in the middle of […]
Choose Your Own Adventure: You Are the CMMC Project Manager

You wake up in a cold sweat. The calendar says “CMMC Readiness QBR,” the invite says “mandatory,” and your inbox says “57 unread: URGENT.” Congratulations: you are now the CMMC Project Manager. You didn’t apply for this job. That’s how you know it’s real. Your mission: get your defense shop to CMMC Level 2 without […]
From Cost Center to Capture Strategy: How Compliance Wins Defense Contracts

For years, “compliance” has been treated like an unavoidable tax on doing business with the Pentagon. Today, with CMMC 2.0 tied directly to award eligibility, it has quietly become one of the strongest competitive levers defense contractors and their MSP partners can pull. According to recent research, only about 1% of defense contractors report being […]
New York: Mass SMS Scam via Hijacked Alert Service

On November 10th, hackers exploited a legitimate mass texting service to send hundreds of thousands of scam messages — including to New York State’s official alert subscribers. This incident, which leveraged public trust in emergency messaging channels, marks an evolution in SMS phishing (“smishing”) scams and raises pressing concerns for individuals and organizations alike. What […]
MSP as Compliance Coach: Educating Clients to Prevent Regulatory Mistakes Before They Happen

Managed service providers are more than just technical troubleshooters — they’re essential compliance coaches, guiding clients through complex requirements and helping them avoid costly mistakes before they happen. Here’s how smart MSPs can position themselves as compliance coaches, using technology and education to drive measurable client success (and how tools like Blacksmith make that journey […]
Free, Open Source Risk Assessment Tool for MSPs and vCISOs
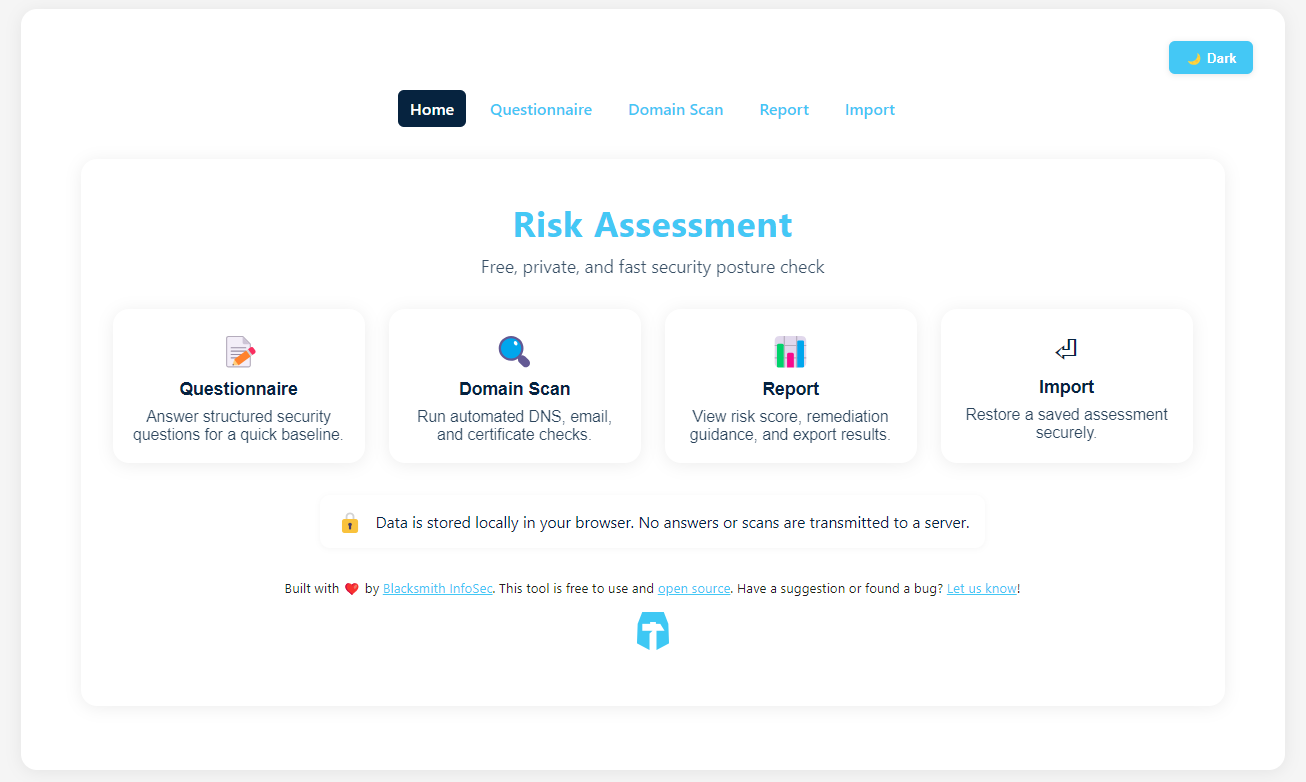
We Just Released a Free Risk Assessment Tool! We’ve been talking with a lot of our partners lately, and a couple of things keep coming up: risk assessments and sales enablement. MSPs want a simple tool to evaluate client risk and show value early in the conversation without getting buried in complexity or licensing costs. […]
The Rise of DragonForce — How Ransomware Cartels Reshape Cybercrime

DragonForce has quickly transformed from the shadows of obscurity into one of the most watched ransomware cartels of 2025, marking a significant evolution in both the scale and style of cyber extortion. First identified by security researchers in 2023, DragonForce initially operated as a Ransomware-as-a-Service (RaaS) enterprise, rapidly gaining notoriety in 2024 with high-profile attacks […]
The Hidden Compliance Crisis: Shadow AI in the Workplace

As artificial intelligence reshapes business operations, one of the most pressing yet underappreciated compliance risks is the rise of Shadow AI — employees using unsanctioned AI tools without organizational oversight. From ChatGPT-style assistants and automated copilots to image generators and workflow agents, these tools have infiltrated workplaces at astonishing rates. According to Microsoft’s 2025 Work Trend […]
