AI Meets Compliance: Using the DOJ’s ECCP as a Security Guardrail

The mandate is everywhere now: “We need to use AI.” Boards want efficiency. Executives want innovation. Vendors are quietly flipping on AI “copilots” in tools you already own. And somewhere in the middle sits security and compliance, being told to adopt AI with little clarity on why, where, or how. Simply saying “no” is no […]
Security Reporting Rules Are Coming for Everyone: How MSPs and vCISOs Prepare Clients for CISA‑Grade Incident Disclosures

The era of “optional” cyber incident reporting is ending, and the operational burden is going to land squarely on managed security providers and vCISOs. CISA is actively refining cyber incident and ransom‑payment reporting rules under CIRCIA, reopening comments, and launching town halls with critical infrastructure sectors to stress‑test what’s realistic. Even if many of your […]
From Alerts to Action: Teaching Execs to Read Cyber Risk Like a Weather Report

Executives are drowning in cyber alerts and starving for decisions. If you want their support, your job isn’t to forward every CVE — it’s to turn threat noise into something they can read like a weather report: clear, comparable, and decision‑ready. What Executives Actually Need (And Don’t) The SOC lives in logs, CVEs, and vendor […]
When Ransomware Becomes a Civic Emergency: What Cities Must Learn from St. Paul

When ransomware hits a city, it stops being an IT story and becomes a public safety problem. In 2025, St. Paul, Minnesota gave us a template for what that escalation looks like. When “IT Outage” Turns into a State of Emergency On July 25, 2025, St. Paul began detecting suspicious activity on its internal networks, […]
Turning a Free Risk Assessment Into Your Client Security Language (Not Just a Compliance Check)
Most MSPs don’t have a language problem with security; they have a translation problem. The Blacksmith Free Risk Assessment gives you a single, reusable grammar you can use to talk about both compliance and security with non‑technical clients in a way that sticks. The problem: no shared language with clients When you walk into a QBR and start talking […]
NIST’s AI Risk Management Framework: What It Is, Why It Exists, and What MSPs Should Know
Artificial intelligence is exploding into every corner of business, but most organizations are still treating AI risk like a side quest instead of part of core governance. The NIST AI Risk Management Framework (AI RMF) is an attempt to fix that by giving a structured, technology‑agnostic way to think about AI risks across the entire […]
Zero-Click Visibility: Securing a Brand When No One Ever Hits Your Site

We’re fast approaching a time when most of your prospects will never land on a site you manage — and that’s a security problem you can’t patch with an agent install. When a CFO types “Is [Client]’s backup provider secure?” or “Best cybersecurity for a 50‑person firm” into Google or an AI assistant, they get […]
Blacksmith Wins Channel Program Q4 Category Leader Badge
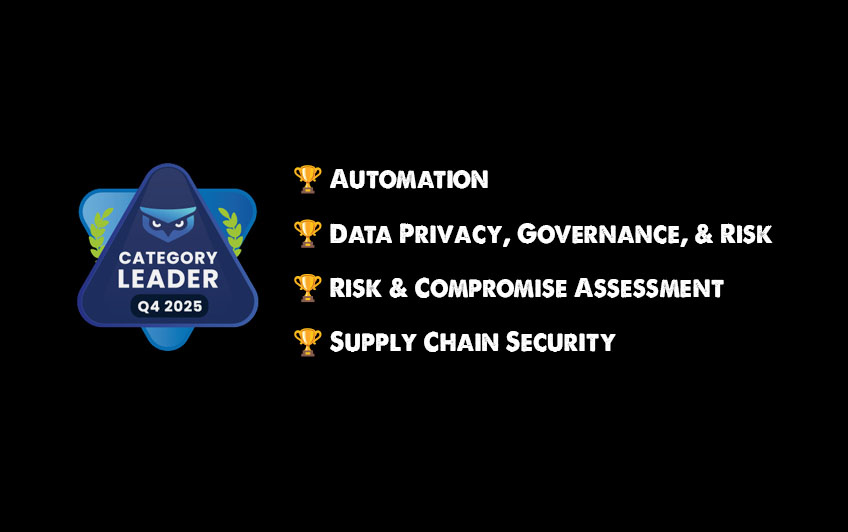
Blacksmith was again awarded the Channel Program’s Category Leader badge, a distinction reserved for the top-rated vendors in the IT channel across more than 80 technology categories! Which Categories Did We Lead? Blacksmith was awarded this badge in the following: Category Leader: Automation Category Leader: Data Privacy, Governance, & Risk Category Leader: Risk & Compromise […]
Operational Ransomware: When Uptime Becomes the Real Crown Jewel

Ransomware is increasingly about stopping a business from functioning, not just stealing or encrypting files. The sectors feeling this most acutely are healthcare, manufacturing, managed service providers, and critical services where every minute of downtime carries a real human or economic cost. When “just” data loss isn’t the point In today’s big-game ransomware operations, the […]
KEV-Driven Patching and “Emergency Directive Fatigue”

Stop chasing every CVE headline; build a KEV-first, risk-based patch playbook If it feels like you’ve been living in a permanent “drop everything and patch” sprint for the last five years, you’re not imagining it. Every week ships a new “critical” CVE, a vendor blast, and at least one headline implying that if you don’t patch […]
