Today we’re going to talk about the National Institutes for Standards and Technology (NIST) Cybersecurity Framework (CSF). It’s an important tool for SMB’s designed to help strengthen their defenses against these cyber risks. NIST CSF has been an industry standard, providing the baseline definition for a well-run cybersecurity program for over a decade. Just like security threats continue to evolve and become more sophisticated, NIST just released updates to CSF to become more sophisticated. NIST CSF 2.0, published on February 26, 2024, updates the original framework with new guidelines to tackle the latest cybersecurity challenges. Staying up to date with the new framework is essential for businesses looking to protect themselves from cyber-attacks, become eligible for or lower their cyber liability insurance rates, and ensure they can handle and recover from any incidents that do occur.
This blog post is your guide to understanding NIST CSF, including the changes introduced with version 2.0. We’ll break down what’s in the framework, why it matters, and how you can apply it to your organization. Whether you’re running a small company, working in cybersecurity, or part of a larger enterprise, getting to grips with NIST CSF is key to creating an effective and resilient cybersecurity strategy. We’ll walk you through the framework’s main elements, show you how it’s used in real life, and outline steps to put it into action. This post will give you the insights you need to make the most of NIST CSF 2.0, helping to keep your organization safe.

Core: The core is organized into functions, categories, and subcategories. Aligning controls into each section.
Tiers: Tiers are ways to measure organizational implementation level of each control with levels being Partial, Risk Informed, Repeatable, and Adaptive.
Profiles: Profiles allow organizations to optimize their security program to their unique needs by capturing the current tier of a control as well as your target tier. This allows you to measure progress towards implementation of the CSF in a way that is aligned to your business needs.
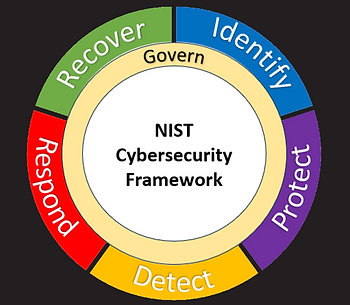
NIST CSF 2.0 maintains the foundational structure established by its predecessor and introduces critical updates to address the increasingly complex cybersecurity landscape. Among these updates is a heightened focus on governance through the introduction of a new core function, underscoring the framework’s commitment to a holistic approach to cybersecurity. This function is called Govern and it represents a shift in the framework’s architecture, emphasizing the strategic alignment of cybersecurity policies and processes with the organization’s overall goals and risk management strategy. The Govern function is designed to ensure that cybersecurity efforts are not siloed but are integrated across all levels of the organization, from executive decision-making to daily operational practices.
The new model now contains 6 core functions: Identify, Protect, Detect, Respond, Recover, and Govern. Here are the full set of core functions and what they mean:

Tier 1: Partial
Awareness and Processes: Organizations at this tier have a limited awareness of cybersecurity risk management. Practices may be ad hoc and not formally established, making them inconsistent and uncoordinated.
Information Sharing: There is minimal information sharing about cybersecurity risks within the organization, leading to siloed knowledge and response strategies.
Risk Management: Risk management practices are often reactive, with limited understanding of the organization’s risk environment. Cybersecurity measures are implemented on an as-needed basis, without comprehensive planning or coordination.
Organizations within this tier typically exhibit an initial, informal approach to cybersecurity controls and practices. From a controls standpoint, these organizations may deploy basic cybersecurity measures, often in an ad-hoc or reactive manner, lacking a formalized structure or comprehensive strategy. Their organizational alignment regarding cybersecurity is characterized by a limited awareness across the workforce, with cybersecurity responsibilities often concentrated within a small group or even an individual, rather than integrated across the organization. This usually leads to either underspending on security if not enough controls are in place, or overspending if controls are deployed that may not align to the organizational risk appetite. Policies, if they exist, are likely to be undeveloped or inconsistently applied, without a clear connection to the organization’s broader risk management objectives. This tier reflects organizations at the beginning of their cybersecurity journey, with significant room for development in terms of establishing systematic, organization-wide cybersecurity practices and policies.
Tier 2: Risk-Informed
Awareness and Processes: At this level, organizations are aware of cybersecurity risks and have begun to implement risk management practices. However, these practices may not be consistently applied across the organization.
Information Sharing: There is more frequent internal communication regarding cybersecurity risks, but it may not be systematically managed.
Risk Management: Risk management practices are approved by management but may not be established as part of the organizational culture. Decisions are informed by risk information but not necessarily driven by a comprehensive risk management strategy.
Organizations within this tier demonstrate a more informed approach to managing cybersecurity risk, albeit with room for further integration and consistency. In terms of controls, these organizations have moved beyond ad-hoc measures, implementing cybersecurity practices that are informed by their understanding of risk but may not yet be fully standardized or systematically enforced across the entire organization. Their organizational alignment shows a greater awareness of cybersecurity importance, with management beginning to endorse and approve cybersecurity practices. However, these practices might not be fully embedded into the organizational culture or uniformly executed across all departments. Policies at this level are likely drafted and in place, reflecting a conscious effort to manage cybersecurity risk. Nonetheless, these policies may not be fully mature or comprehensively cover all aspects of cybersecurity. Essentially, Tier 2 organizations recognize the value of cybersecurity and have started to implement relevant measures but have not yet achieved a fully integrated, organization-wide approach to cybersecurity risk management.
Tier 3: Repeatable
Awareness and Processes: Organizations have formalized their cybersecurity practices, with policies and procedures that are consistently and repeatedly applied across the organization.
Information Sharing: There is a structured approach to internal and external information sharing regarding cybersecurity risks. The organization actively engages in sharing best practices and collaborating on cybersecurity issues.
Risk Management: Cybersecurity risk management is integrated into the organizational culture. Practices are regularly reviewed and updated based on a continuous assessment of cybersecurity risks and environmental changes.
Organizations within this tier exhibit a more mature approach to cybersecurity, characterized by well-established, formalized practices and policies. Controls in these organizations are systematically implemented and are part of a consistent and repeatable process that is integrated across the organization. There is a strong organizational alignment with cybersecurity, where practices are not only approved by management but are also well-understood and adhered to by all members of the organization, reflecting a significant cultural integration of cybersecurity awareness and practices. Policies at this level are comprehensive, detailed, and actively enforced, with clear procedures for their application and review. These policies are supported by ongoing training programs to ensure that all employees are informed and capable of contributing to the organization’s cybersecurity posture. Tier 3 organizations have effectively incorporated cybersecurity into their risk management strategies, ensuring regular reviews and updates of cybersecurity practices in response to evolving threats and business needs. This tier indicates a proactive stance towards cybersecurity, with organizations actively managing their cyber risk in a strategic and dynamic manner.
Tier 4: Adaptive
Awareness and Processes: At the highest tier, organizations have adaptive risk management practices that evolve in response to new cybersecurity threats and organizational changes. Cybersecurity risk management is deeply ingrained in the organizational culture.
Information Sharing: There is proactive and real-time information sharing about cybersecurity risks, both internally and with external partners. The organization contributes to and benefits from broader industry knowledge of cybersecurity threats and defenses.
Risk Management: Risk management practices are agile and informed by lessons learned from past security incidents and predictive indicators of future threats. The organization continuously adapts and responds to cybersecurity risks in a dynamic and effective manner, ensuring that cybersecurity practices not only defend against current threats but also anticipate and mitigate future challenges.
Organizations within this tier represent the pinnacle of cybersecurity maturity, characterized by adaptive, proactive, and advanced cybersecurity practices that are fully integrated into the organizational culture and operational processes. Controls within these organizations are not just systematically implemented but are also continuously monitored, evaluated, and adjusted based on current and predictive cyber threat intelligence. This enables a dynamic and agile response to emerging threats. Organizational alignment at this level is comprehensive, with cybersecurity being a central component of the organization’s strategic planning, driven by executive leadership and embraced across all levels of the organization.
Policies in Tier 4 organizations are sophisticated, fully institutionalized, and aligned with both the organization’s strategic goals and the broader cybersecurity landscape. These policies are subject to regular and rigorous review processes that ensure they remain effective and relevant. Moreover, Tier 4 organizations engage in active information sharing and collaboration with external entities, contributing to and benefiting from the wider cybersecurity community. This tier reflects an organization that not only anticipates cybersecurity challenges but also innovates and leads in the development of new cybersecurity standards and practices. Such organizations are agile and resilient, capable of adapting their cybersecurity strategies in real-time to mitigate risks from sophisticated and rapidly evolving cyber threats.
These tiers provide a framework for organizations to assess their current cybersecurity practices and plan for progression towards more advanced, proactive, and adaptive cybersecurity risk management strategies.

NIST Cybersecurity Framework (NIST CSF) Profiles serve as customizable benchmarks that guide organizations in tailoring the framework’s standards to their specific operational needs, risk appetite, and objectives. By developing a “Current Profile” to map out existing cybersecurity practices and a “Target Profile” to delineate desired security outcomes, organizations can perform a gap analysis to pinpoint areas needing improvement. This process allows for the prioritization of cybersecurity initiatives, facilitating a strategic approach to closing gaps between current capabilities and future goals. Profiles enable a cycle of continuous improvement and adaptation to evolving cybersecurity threats and business requirements, offering a flexible tool that can be adjusted to suit various industries and organizational sizes, ensuring cybersecurity measures are both effective and aligned with business objectives in a practical and actionable manner.

NIST CSF 2.0 emerges as a critical evolution in cybersecurity management, reflecting the dynamic nature of cyber threats and the growing sophistication required to counter them. Understanding and implementing the updated framework is not just about safeguarding assets but also about fostering a culture of security that permeates every level of the organization. From the foundational core functions, including the new Govern function, to the detailed tiers and customizable profiles, NIST CSF 2.0 offers a comprehensive roadmap for enhancing cybersecurity postures. It underscores the necessity of a strategic approach to cybersecurity, one that is adaptive, aligned with business needs, and capable of evolving in response to emerging threats. As organizations navigate the complexities of the digital landscape, adopting NIST CSF 2.0 is a crucial step towards achieving not only a resilient cybersecurity strategy but also a competitive edge. The journey from Tier 1 to Tier 4 illustrates a path of maturity and integration of cybersecurity practices, with each tier building upon the last, ensuring that organizations can measure progress and align their cybersecurity efforts with their specific business objectives. Leveraging NIST CSF 2.0, organizations are equipped to transform their cybersecurity challenges into opportunities for growth, innovation, and strengthened trust with stakeholders.
Blacksmith InfoSec gives you all the tools to align your security program with NIST CSF and take yourself to Tier 4 in short order. We offer comprehensive, regularly updated security policies that you can customize in minutes – and we continuously evaluate our policy templates to help make sure that your security policies will be compliant with NIST CSF. Our security awareness training is refreshed regularly to keep your users apprised of the threats facing your business and how to defend against them. We offer a basic LMS to track user acknowledgements of your policies and completion of security awareness training. The tool automatically generates a security roadmap that is tailored to your organization and prioritized to make you successful. And the built in risk management tool allows you to track your organization’s risks holistically, ensuring better informed decision making.